In some situations it could happens to use a client vpn to access in some lan or network segment to manage or interacts with systems that are isolated from external access. In this post I’ll show howto do it with pfSense.
Installation and configuration
- new virtual machine
- GuestOS: Other FreeBSD 64bit
- Hardware (min):
- 1 vCPU
- 1 GB RAM
- 5 GB HDD
- 2 network device (leave not configured)
- no Floppy Disk
Attach ISO Image pfSense and start installation
- Boot Multi User
- Invoke installation with I button
- Optional change keyboard map
- Choose quick and easy install
- Choose standard kernel
- Reboot
Optional: At this moment you could make a template keeping in mind that due to FreeBSD support (incomplete) you’re not able to configure ip settings during VM deployment.
Configure networking interfaces
Prerequisites:
- Public IP to make this connection available over internet
- local lan IP
- a logical lan available (means not in conflict with other lan) for clients
Configure wan and lan and wan using options in main menu:
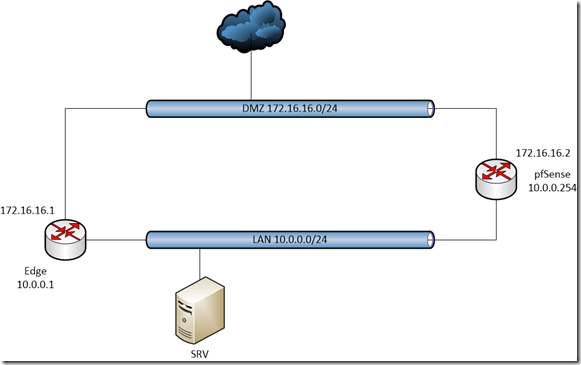
This could be the scenario after all configurations are done:
Configure VPN Service
Use a client (or a server with gui) to connect to the web ui. Note: the default credential are admin/pfsense… after first login you should change this password!
Create or add server certificate:
- move to system –> cert manager –> CAs
- Create an internal ca with local country and organization data
- move to system –> cert manager –> certificate
- create an internal certificate wi Internal CA as authority
- Note that you should insert more alternative names depending on NAT, DNS entry, etc and certificate type must be Server
Now it’s time to configure VPN
- VPN – openvpn – servers-add
- choose the right access mode: in this case (client to lan) User Auth is enough
- the defaults are: protocol UDP, tun, WAN and port 1194
- use CIDR logical lan for client in ipv4 tunnel network
- use 10.0.0.0/24 (aka LAN) in IPv4 Local network
- optional: flag Provide DNS server list to clients
- optional: you could insert routes into custom options
pfSense is well-made system made with good security level; for this reason you have to set some rules to enable users to connect with vpn and to the other systems in lan:
- Move to Firewall –> Rules –> WAN
- Add this rule:
- Protocol IPv4 TCP
- Source *
- Port 1194
- Destination This Firewall
- Port 1194
- Gw *
- Queue none
- To enable OpenVPN clients to connect to LAN ip move to Firewall –> Rules –> OpenVPN
- Add this rule:
- Protocol IPv4 TCP
- Source *
- Port *
- Destination *
- Port *
- Gw *
- Queue none
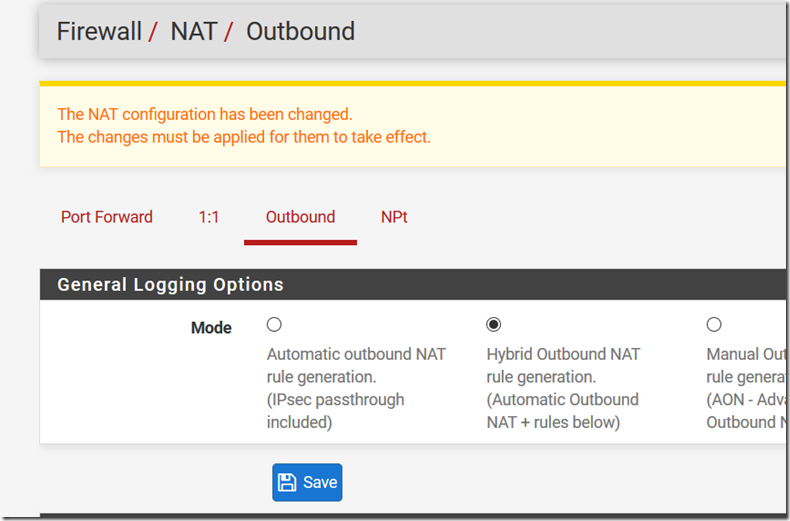
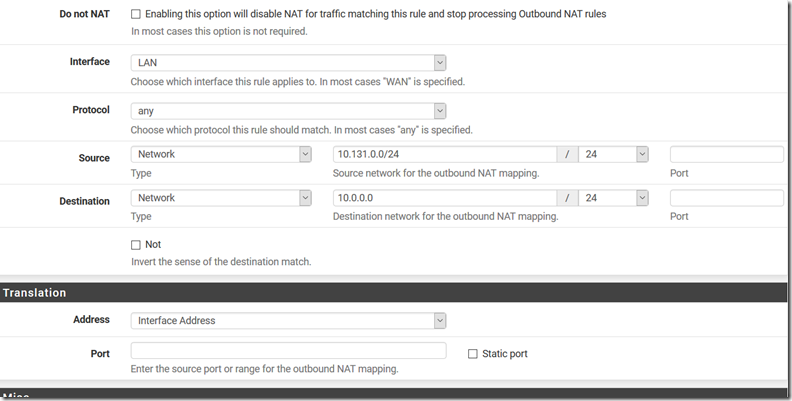
Because OpenVPN is not the default router it’s mandatory that every connected client must be masquerate by firewall ip. Move to Firewall –> NAT –> OpenVPN then configure Outbound Mode Hybrid
…and add masquerading rule from every client connecting. This because every server in LAN has default gw rule pointing to edge. For this reason the only way to connect is using the pfSense ip which has a LAN ip.
The simplest way to distribute client-to-lan vpn to users is:
- Issue new user in System -> User manager -> Users>
- Share configuration data for Open VPN client.
I suggest to install opnevpn-client-export package to speed-up vpn client delivery process
Test the VPN simply downloading openvpn client and export configuration (or download a packaged version directly from VPN –> OpenVPN –> Client Export ) and connecting with it’s option under openvpn client connection option.