After some days from the announcement of this vulnerability, some updates coming out from official channels and community blog are providing further information about patches and resolutions, clarifying also where to focus the attention where you don’t need to rush patching.
I’ve already described (or better I linked some resources) the mechanism and the degree of danger where the unauthorized read-only action could cause a data breaches that is really difficult to identify and quantify.
Updates from VMware vSphere
An important update in KB 52085 is showing how to mitigate the vulnerability acting from hypervisor level. In order to enable this feature is important update both CPU microcode (finally available from hardware vendors and Intel) and hypervisor. Before update it’s important also take a look at https://kb.vmware.com/s/article/52345 for resolution of side effect of application of ESXi patch ESXi650-201801402-BG, ESXi600-201801402-BG against Spectre vulnerability. In fact recent sightings are notified by Intel that may affect some of the initial microcode patches that provide the speculative execution control mechanism for a number of Intel Haswell and Broadwell processors. The solution is remove the exposure of speculative-execution for patched OS VM until Intel provides a new micro-code update.
Verifying the issue
There’s a lot of scripts that, running at operative system level, could check if your system is affected to this vulnerability, investigating both hardware and OS level.
I tested the use SpeculationControl Module available for Powershell. The installation is very simple:
|
1 |
Install-Module -Name SpeculationControl |
Then issue the command:
|
1 |
Get-SpeculationControlSettings |
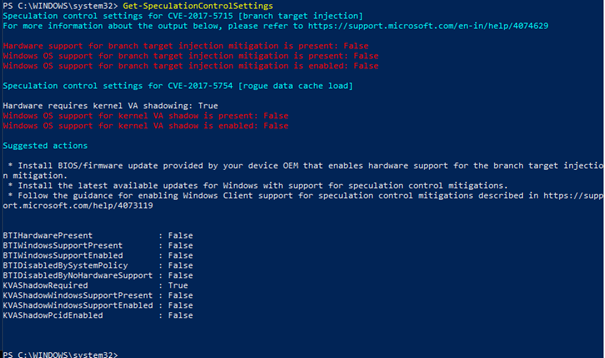
Here the result of a vulnerable system:
Here the official documentation that could let you better understand the results: https://support.microsoft.com/en-in/help/4074629/understanding-the-output-of-get-speculationcontrolsettings-powershell
Source: https://www.powershellgallery.com/packages/SpeculationControl/1.0.4
Automating the check
Obviously the SpeculationControl module could be implemented in a script to gather the situation of the whole data-center workloads. There are two methods:
- Automation based on PowerShell (an example well-explained here: https://blogs.technet.microsoft.com/ralphkyttle/2018/01/05/verifying-spectre-meltdown-protections-remotely/ )
- Automation based on PowerCLI using Invoke-VMScript Cmdlet with the same mechanism used to gather another vulnerability: https://blog.linoproject.net/tech-tip-how-to-check-windows-patch-against-wannacry-using-powercli/
From vSphere side, the application of patch and/or workaround for “Sightings” is well explained in the Lam’s posts here: https://www.virtuallyghetto.com/2018/01/verify-hypervisor-assisted-guest-mitigation-spectre-patches-using-powercli.html and here https://www.virtuallyghetto.com/2018/01/automating-intel-sighting-remediation-using-powercli-ssh-not-required.html
The state from OS level to cloud level
Ubuntu, after some hesitations, finally has rolled out a patch for 17.10, 16.04LTS, 14.04 LTS and 12.04; to mitigated simply issue
|
1 |
sudo apt-get update && sudo apt-get full-upgrade |
RedHat/CentOS has already provided the patch in a security update (aka “errata”). Check here: https://access.redhat.com/security/vulnerabilities/speculativeexecution
Apple MacOS has provided a patch for Sierra, High Sierra and El Capitan. (https://support.apple.com/en-us/HT208331)
Amazon AWS, Azure and Google infrastructures have been updated.
For knowledge purpose, check this interesting post about performance imapact in Google Cloud Platform (GCP): https://www.blog.google/topics/google-cloud/protecting-our-google-cloud-customers-new-vulnerabilities-without-impacting-performance/