Remote management with PowerShell
In this post I’ll show how to connect to remote systems using local/AD credential with Powershell. To successfully connect to remote system you should have a local/AD Administrator account be able to gain Admin privileges to remote server.
This how-to is tested on Windows Server 2012 and Windows Server 2016.
Enabling Remote access
- Using a remote console, on the remote system launch powershell with Administrator rights
-
1Enable-PSRemoting –Force
-
1Set-Item WSMan:/localhost/Client/TrustedHosts –Value * –Force
-
1Restart-Service WinRM
Client setup
On the desktop system there are few steps to follow before trying a connection:
- Open PS with Administrator rights
- Add servername or IP in the thrusted hosts:
-
1Set-Item WSMan:/localhost/Client/TrustedHosts –Value * –Force
-
- Start WinRM Service with net start WinRM
Time to connect
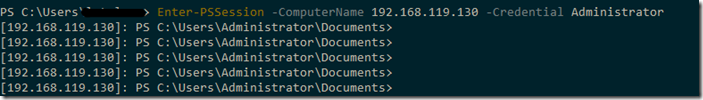
Enter in remote simply using this syntax:
|
1 |
Enter-PSSession -ComputerName "servername or IP" -Credential servername/Administrator |
Test and troubleshooting
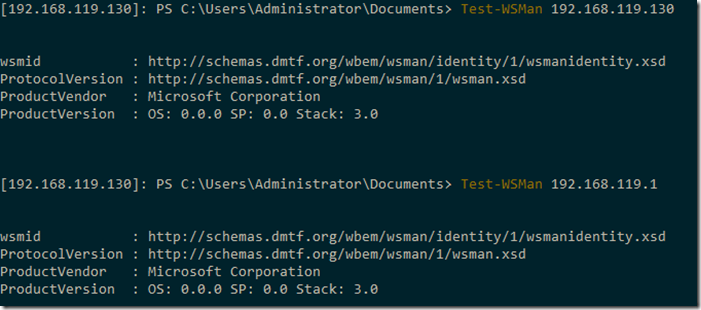
To ensure that connection is correctly configured and matched with trusting hosts, you could use Test-WsMan cmdlet:
In some cases you should configure firewall policy to allow incoming the following incoming connection:
- TCP/5985 = HTTP
- TCP/5986 = HTTPS
Note and use-case
It’s important to authorize people and allowed host to restrict the access only for domain/system administrator. For this reason is important to specify the a host fqdn or ip in TrustedHosts WSMan entry.
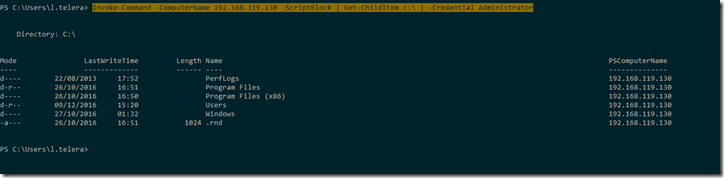
Using powershell with Invoke-Command is an interesting way to manage multiple hosts or make repetitive tasks across multiple hosts.
|
1 |
Invoke-Command –ComputerName “servername or IP” -ScriptBlock { “Script here” } -Credential Administrator |
There is an interesting article here about clear and secure ports: https://blogs.technet.microsoft.com/christwe/2012/06/20/what-port-does-powershell-remoting-use/
Thanks to How-to Geek for the guide http://www.howtogeek.com/117192/how-to-run-powershell-commands-on-remote-computers/